Recent Posts
Way to Darker side of internet | Best way to access darknet
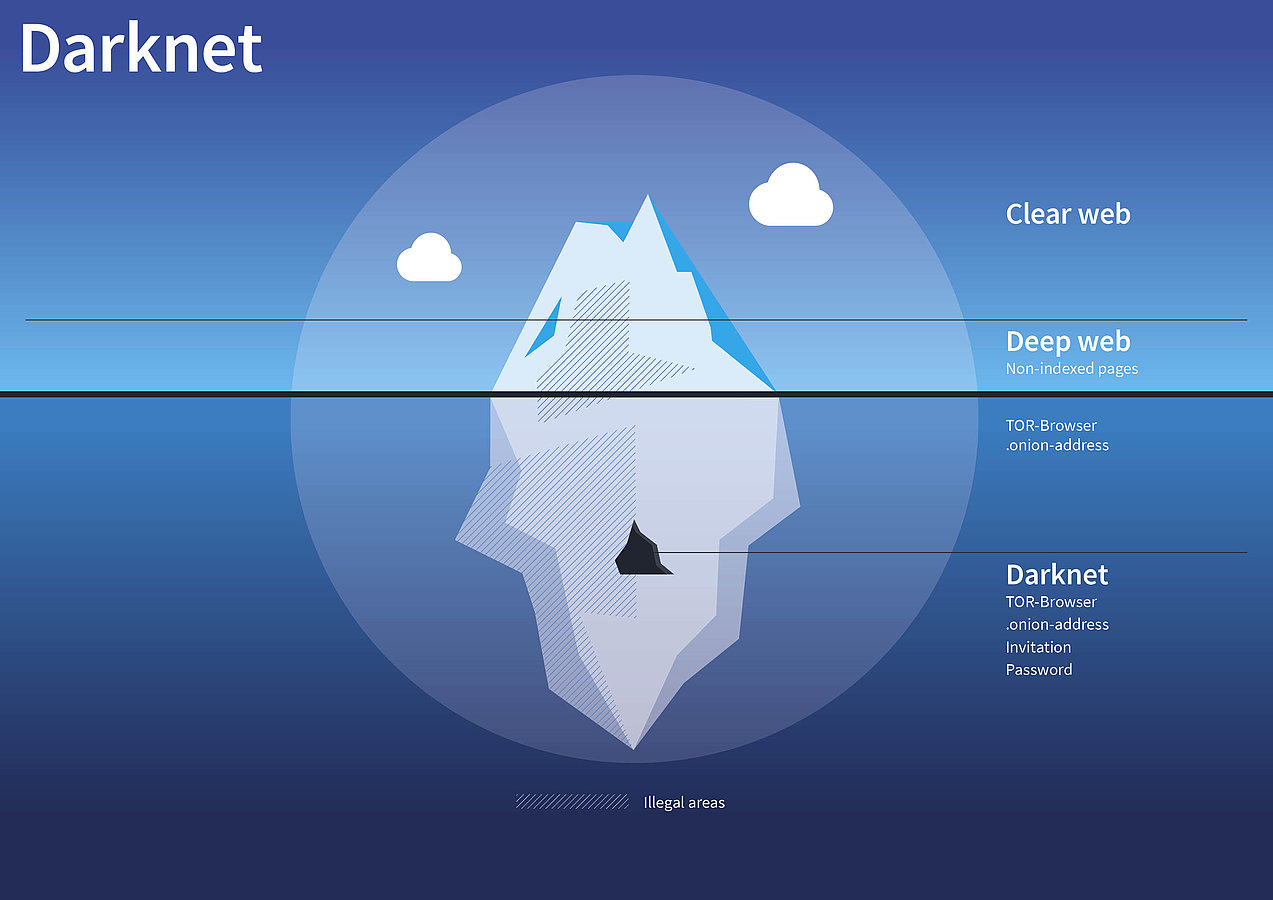
What is a Virtual Private Network? Before we explore what VPNs are, let’s establish the link between the internet and security. Most public networks such as the Wi-Fi that you’re using in your office are susceptible to traffic analysis. There are always unseen “online” eyes everywhere if you are using these networks. Traffic analysis may emanate from government agencies such as FBI or CIA—that may interested in monitoring your online movements—or private corporations that want to target you with their “boring” products or services. But that’s not all. The majority of Internet Service Providers (ISPs) may also be monitoring your internet activities to promote their services. This means that at the very least, you should protect your data such as credit card details, usernames, and passwords particularly if you’re using a public network. The Tor and VPN can help you protect your private data as you remain anonymous while accessing the internet. So, what is a VPN? A VPN is a network connection that is established to provide a secure link to another location (usually a remote location). A VPN creates the illusion that you are connecting from a different place, therefore, malicious internet users may not know what’s being transmitted across the internet. Ideally, your computer will create an encrypted virtual tunnel that connects to the VPN server from where the entire internet traffic is channelled. Once the private connection has been linked to the VPN server, all the communication that takes place on the network will appear as though coming from the VPN server, but in the real sense, it’s coming from your computer. This keeps your data from being exposed to eavesdroppers that may be interested in tapping the data in transit. Why may you want to use a VPN instead of the public networks? First, you can use a VPN to connect securely to any remote network through the web. If you have employees who want to access some files, applications and other resources such as printers, then installing a VPN will be helpful if you don’t want to compromise on security.in fact, you can set up a VPN to access your home network if you’re ever traveling. Second, VPNs can help to connect several networks together in a secure manner. In fact, you can use a VPN to share servers and other networked resources such as printers that may be located in different places. If you’re an organization, then VPN’s can help you connect multiple intranets for the promotion of your bottom line. Third, VPNs can help you improve your online privacy and anonymity. If you’re connected to a public network such as Wi-Fi, then the communication may be untrusted. A VPN can help you secure such communication because it encrypts the internet traffic, therefore, helping you to maintain your privacy while you remain anonymous while online. Lastly, a VPN can help to circumvent regional internet restrictions—what’s commonly known as geo blocking—on some sites. Some authoritarian governments or even private corporations may place restrictions on some sites. VPN’s can help you to bypass such restrictions. In fact, several journalists have used VPNs to sidestep state sponsored website censorship in the majority of authoritarian states. What is the difference between TOR and VPNs? The differences between Tor and VPNs are multi fold. First, Tor networks contain several volunteer nodes that transmit data from the entry computer (source) to the exit node which is the destination computer. It allows the client computers to conceal their status through configurations of the volunteer nodes (Tor servers) which links up with the Tor workstations. The Tor Server doesn’t need to provide its IP address and so does the client. Instead, the network uses the onion address—a 16 character code that a client has to enter instead of the conventional URL. On the other hand, VPN networks don’t use volunteer nodes to relay data between the client and the server. It’s basically an into-the-tunnel and out-of-the-tunnel network that encrypts whatever communication is taking place. In other words, if you trust the VPN provider for data privacy and anonymity, then it is. Second, Tor networks tend to be slow compared to VPNs. This is because the information that is sent from one computer to another must be encrypted every time it passes a volunteer Tor node. This slows down the communication process. Although encryption is also handled in VPNs, the encryption process doesn’t occur at every node. Third, Tor networks will always guarantee privacy and anonymity. This is because of the manner they operate. For instance, the Tor server doesn’t need to provide its IP address and so does the client. Instead, the network uses the onion address—a 16 character code that a client has to enter instead of the conventional URL. This will guarantee your privacy and anonymity. On the other hand, the type of VPN provider you choose for your services dictates the quality of the services. Therefore, it’s vital that you select a quality VPN provider that doesn’t store communication logs. This is because the communication logs can still be accessed therefore exposing the communication between the client and the server. Finally, Tor networks can help you to access the Deep Web. The Tor protocol enables the clients to hide their status (IP addresses) by configuring the server to link up with the Tor workstations using the Tor relay. The server doesn’t need to provide its IP address and so does the client. Instead, the Tor network uses the onion address that a client has to enter instead of the conventional URL. Since these networks have several famous Deep Web data, clients can access them through the Tor relay. Conversely, VPNs can’t access any Deep Web or Darknet. Other protocols that can access the Deep Web Now that you’ve learned how Tor works and the differences between Tor and VPNs, let’s dig deeper to find out which other protocols can be used to access Deep Web. Below are other protocols that can enhance privacy and anonymity while online while also allowing users to access Deep Web: #1: I2P I2P, which is an acronym for Invisible Internet Project, is a protocol that was started way back in in 2003, to promote anonymity of internet users. All I2P networks aren’t accessible from any regular computer unless special software is installed on such computers. When you install I2P software on your computer, you’ll begin to route internet traffic through the I2P system just like a Tor relay. The I2P system encrypts the communication by creating a distributed, decentralized and dynamic network that enables secure communication between the client and server. You can also use the I2P network to circumvent state sponsored website censorship in the majority of authoritarian states. Is I2P network different from Tor? Yes. I2P networks route web traffic differently compared to Tor. At the heart of I2P is packet-based routing system as opposed to the Tor’s circuit-based routing. This means that there’s no dedicated route between the client and the server as we saw in Tor relays where the Tor servers establish a dedicated path through which the traffic is routed. Because of packet-based routing, the traffic can be routed dynamically in a distributive manner as opposed to the Tor relay. This offers a higher level of reliability to the network. In addition, the I2P network doesn’t rely on the trusted directory service to obtain its route information. Instead, the network routes are created dynamically and updated regularly. #2: Freenet Freenet is a fully peer-to-peer, distributed, anonymity publishing network that offers secure means to store data. Besides providing anonymity, Freenet allows internet users to create applications that ride on its platform to develop more generic and anonymous communications. Such applications include static websites and online message boards. Contrasted with to I2P, Freenet provides some substantial benefits. Besides, its distributed data store, it allows users to get the content that’s published by others even if the publisher isn’t connected to the internet. While there’s an overlap of users who simply want to share data with each other anonymously in Freenet, I2P systems don’t offer such services to their users.
View MoreWeb Server Vulnerability Scanners Used by Professional Bug Hunters
Web Server Vulnerability Scanners Web Application Vulnerability Scanners are automated tools that scan web applications, normally from the outside, to look for security vulnerabilities such as Cross-site scripting, SQL Injection, Command Injection, Path Traversal and insecure server configuration. This category of tools is frequently referred to as Dynamic Application Security Testing (DAST) Tools. A large number of both commercial and open source tools of this type are available and all of these tools have their own strengths and weaknesses. If you are interested in the effectiveness of DAST tools, check out the OWASP Benchmark project, which is scientifically measuring the effectiveness of all types of vulnerability detection tools, including DAST. SUCURI SUCURI is one of the most popular free website malware and security scanner. You can do a quick test for malware, blacklisting status, injected SPAM, and defacements. SUCURI also helps to clean and protect your website from online threats and works on any website platforms, including WordPress, Joomla, Magento, Drupal, phpBB, etc. Netsparker Web application security testing tools in complex environments should work together seamlessly with existing systems. You can integrate Netsparker with market-leading CI/CD solutions and issue trackers to use the web application security scanner in your DevSecOps/SecDevOps environment and follow the best practice shift-left paradigm (test early and test often). Such an approach will let you eliminate security vulnerabilities as early as possible, helping you save a lot of resources. You can also easily use Netsparker together in the SDLC with other security tools, for example, source code analyzers. Vega Vega is another free open source web vulnerability scanner and testing platform. With this tool, you can perform security testing of a web application. This tool is written in Java and offers a GUI based environment. It is available for OS X, Linux and Windows. It can be used to find SQL injection, header injection, directory listing, shell injection, cross site scripting, file inclusion and other web application vulnerabilities. This tool can also be extended using a powerful API written in JavaScript. While working with the tool, it lets you set a few preferences like total number of path descendants, number of child paths of a node, depth and maximum number of request per second. You can use Vega Scanner, Vega Proxy, Proxy Scanner and also Scanner with credentials. If you need help, you can find resources in the documentation section: Documentation: https://subgraph.com/vega/documentation/index.en.html Wapiti Wapiti is also a nice web vulnerability scanner which lets you audit the security of your web applications. It performs black-box testing by scanning web pages and injecting data. It tries to inject payloads and see if a script is vulnerable. It supports both GET and POSTHTTP attacks and detects multiple vulnerabilities. It can detect following vulnerabilities: File Disclosure File inclusion Cross Site Scripting (XSS) Command execution detection CRLF Injection SEL Injection and Xpath Injection Weak .htaccess configuration Backup files disclosure and many other Wapiti is a command-line application. So, it may not be easy for beginners. But for experts, it will perform well. For using this tool, you need to learn lots of commands which can be found in official documentation. Download Wapiti with source code: http://wapiti.sourceforge.net/ Wfuzz Wfuzz is another freely available open source tool for web application penetration testing. It can be used to brute force GET and POST parameters for testing against various kinds of injections like SQL, XSS, LDAP and many others. It also supports cookie fuzzing, multi-threading, SOCK, Proxy, Authentication, parameters brute forcing, multiple proxy and many other things. You can read more about the features of the tool here: http://code.google.com/p/wfuzz/ This tool does not offer a GUI interface, so you will have to work on command line interface. Download Wfuzz from code.google.com: http://code.google.com/p/wfuzz/ Detectify Fully supported by ethical hackers, the Detectify domain and web application security service offers automated security and asset monitoring, being able to detect more than 1500 vulnerabilities. Its vulnerability scanning capacity includes OWASP Top 10, CORS, Amazon S3 Bucket, and DNS misconfigurations. The Asset Monitoring service continuously monitors subdomains, searching for hostile takeovers and alerting if anomalies are detected. Detectify offers three pricing plans: Starter, Professional, and Enterprise. All of them start with a 14-day free trial, which you can take without using a credit card. Pentest-Tools The website vulnerability scanner is one of a comprehensive set of tools offered by Pentest-Tools that comprise a solution for information gathering, web application testing, CMS testing, infrastructure testing, and SSL testing. In particular, the website scanner is designed to discover common web application vulnerabilities and server configuration issues. The company offers a Light version of the tool, which performs a passive web security scan. It is capable of detecting many vulnerabilities, including insecure cookie settings, insecure HTTP headers, and outdated server software. You can perform up to 2 free, full scans of your website to get a comprehensive assessment. The results will tell you about vulnerabilities such as local file inclusion, SQL injection, OS command injection, XSS, between others. WebScarab WebScarab is a Java-based security framework for analyzing web applications using HTTP or HTTPS protocol. With available plugins, you can extend the functionality of the tool. This tool works as an intercepting proxy. So, you can review the request and response coming to your browser and going to thw server. You can also modify the request or response before they are received by server or browser. If you are a beginner, this tool is not for you. This tool was designed for those who have a good understanding of HTTP protocol and can write codes. Webscarab provides many features which helps penetration testers work closely on a web application and find security vulnerabilities. It has a spider which can automatically find new URLs of the target website. It can easily extract scripts and HTML of the page. Proxy observes the traffic between server and your browser, and you can take control of the request and response by using available plugins. Available modules can easily detect most common vulnerabilities like SQL injection, XSS< CRLF and many other vulnerabilities. Source code of the tool is available on Github: https://github.com/OWASP/OWASP-WebScarab Download WebScarab here: https://www.owasp.org/index.php/Category:OWASP_WebScarab_Project
View MoreUbertooth One: A Bluetooth Network Hacking Tool
Ubertooth One: A Bluetooth Network Hacking Tool bertooth One is a cheap, open-source Bluetooth network sniffer. Unlike Wi-Fi, which has had a wide range of free network monitoring tools for years, Bluetooth has remained pretty closed. Michael Ossman is about to change this, with his Ubertooth Kickstarter project. The Ubertooth One is a USB plug with an antenna, and a ARM Cortex-M3 processor-based board in-between. Plug it into your computer and you can use it with various wireless monitoring tools like Kismet. The Ubertooth allows you to use Bluetooth in monitoring mode. This "promiscuous" mode makes the radio pass everything that it picks up onto the host computer. Normally, wireless receivers will ignore anything not addressed to them. In promiscuous mode, you can sniff and gather data meant for other devices. These tools can be used for testing network security, or for hacking. Kismet, for example (and derivatives like the Mac OS X version KisMac) can be used to crack Wi-Fi networks' passwords. Until now, Bluetooth monitoring hardware would cost upward of $1,000. Ossman's device will cost just $100 and, because both the software and hardware are open-source, you can build your own. There are three major components of Project Ubertooth: hardware: The hardware design of Ubertooth One is quite stable. firmware: This is software that executes on the ARM processor on the Ubertooth One itself. This page assumes that you have the USB bootloader plus bluetooth_rxtx firmware installed on your board (which is typically what is installed at the time of assembly). The bluetooth_rxtx firmware is moderately stable but is likely to be enhanced as time goes on. host code: This is software running on a general purpose computer connected to the Ubertooth One via USB. The sample host code for Project Ubertooth is in active development and will likely change a great deal in the coming months. Ubertooth One is a development platform. The true power of the device is best realized when you start writing your own software and adapting it to your needs. If you are just getting to know the board, however, it can be helpful to try out open source code that others have made available. This guide will help you get started with your Ubertooth One by introducing you to some useful host code from the Ubertooth software repository. LAP SNIFFING Bluetooth packets start with a code that is based on the Lower Address Part (LAP) of a particular Bluetooth Device Address (BD_ADDR). The BD_ADDR is a 48 bit MAC address, just like the MAC address of an Ethernet device. The LAP consists of the lower 24 bits of the BD_ADDR and is the only part of the address that is transmitted with every packet. The most important passive Bluetooth monitoring function is simply capturing the LAP from each packet transmitted on a channel. LAP sniffing allows you to identify Bluetooth devices operating in your vicinity. In order to sniff LAPs, you'll have to compile the tools in host/bluetooth_rxtx. These are command line programs intended to work with the bluetooth_rxtx firmware installed on your Ubertooth One. Follow the instructions in the README file in that directory to install the the prerequisite libbtbb, a library for Bluetooth baseband functions. You can install libbtbb from a file release rather than git if you prefer. Once libbtbb is installed, just type "make" in the host/bluetooth_rxtx directory to compile the tools there. Then make sure your Ubertooth One is plugged in and execute: $ ./ubertooth-lap You should see various random LAPs detected. Due to uncertainties in identifying Bluetooth packets without prior knowledge of an address, it is normal for this process to identify false positives at a rate of roughly 20 per minute. When you see the same LAP detected more than once, that is very likely an actual Bluetooth transmission. Generate some Bluetooth traffic and enjoy the show. I like to use a mobile phone or other Bluetooth device to perform an inquiry (usually called "find new Bluetooth devices" or something similar) to make sure that everything is working properly. An inquiry should produce lots of packets with the LAP 0x9e8b33. KISMET More advanced Bluetooth sniffing has been implemented in the form of a plugin for Kismet, the venerable 802.11 monitoring tool. In order to compile the Kismet-Ubertooth plugin, you will need a Kismet source tree matching the installed version. The easiest way to make this work is to uninstall any binary Kismet installation you may have installed and then download the Kismet source and follow the instructions to compile and install from the fresh source code. Once Kismet is installed, follow the instructions in host/kismet/plugin-ubertooth/README to install and use the plugin. Notice that Kismet-Ubertooth identifies not only the LAP but also the 8 bit Upper Address Part (UAP) of detected devices as it is able. This is done by analyzing the timing and other characteristics of multiple packets over time. Another advantage of Kismet is that it dumps complete decoded packets to a pcapbtbb file that can be read with a Wireshark plugin that is distributed with libbtbb. Full packet decoding is only possible when the packet's UAP has been determined.
View MoreLearn the ABCD of Dos attacks
Types of DoS Attacks Denial of service as an attack vector is quite interesting because every machine ever made and most likely every machine that will ever be made is vulnerable to a denial of service in some form, and some systems are just more difficult than others to "DOS". This is because every machine has a finite set of resources that it can use to process data, by giving a machine more data than it can possibly process and in some way sustaining that you are causing a denial of service as the machine is paralyzed performing an impossible task and struggling to keep up with its other intended functions. If it helps, think of an old computer. Now think of installing a modern, resource-intensive application on that machine and trying to run it. Do you notice now how that computer is seemingly in limbo for 15-20 minutes as it tries to run that application? We are now effectively '~DoS-ing" that old computer by giving it way too much to process. If after the computer catches up and becomes responsive again, we launch another such application, and another, and then another, we can keep that machine unusable for a very long time. If we keep on doing this, vital services may start to crash and the machine might become unstable and unusable until we reboot it.Whereas most of the "classic" DoS techniques that we will be discussing in this section are the result of programmatic mistakes from software vendor implementation of the IR and other software, resource exhaustion and service termination are still the common thread for most DoS attacks Ping of Death The Ping of Death DoS attack deals with IP fragmentation.When a datagram is processed from a sending to a receiving device, it may be passed through many different physical networks. Each network may have its own frame formats and specific limits that determine the maximum amount of data that can be transmitted (per datagram). For example, Ethernet limits this amount to 1,500 bytes. That is Ethernet's maximum transmission unit (MTU). If the IP must send data that exceeds a specific network's MTU, fragmentation can occur. Therefore, fragmentation is simply the process of dividing a datagram into smaller fra2ments which are each sent separately. Each fragment becomes its own datagram and is sent independent of the other fragments. They can all go their own way and take unique, separate paths to the final destination. If even one fragment does not arrive, the receiving device must discard the remaining fragments when the fragmentation timer reaches zero. As IP is a connectionless service, it's dependent on higher-layer services to force a retransmission of the datagrams. IP is dependent upon several fields to know whether datagrams have been fragmented and how to properly reassemble them. These fields include: The ID field The more bit Fragmentation offset The Ping of Death utilizes an oversized packet that is illegally fragmented. RFC 791 specifies that IP packets can be up to 65,535 octets long (2^16- 1), which includes the length of the IP header (usually 20 octets if no IP options are specified). An Internet Control Message Protocol (ICPM) Echo Request (ping) is carried inside an IP packet and has a header length of 8 octets followed by the length of the data octets in the ping request. So, the maximum size for the data area of a ping can be 65,507 (65,535 - 20 - 8 = 65,507). A Ping of Death carries a data payload that is greater than this maximum size (greater than 65,507 octets). Of course, as was previously mentioned, sending a ping that size will cause the packet to fragment. When the fragments are reassembled on the victim's system, it can cause a buffer overflow on older systems. As a result, the IP stack will crash and the system will become unresponsive on the network. This attack was first seen in 1996. At that time, a lot of systems were susceptible to it. Today this attack is largely of historical significance, or can perhaps be run against legacy systems. Teardrop Attack Fragmentation, as illustrated in the previous section, is a necessary mechanism of IP; however, overlapping fragments can also offer an attacker a means of slipping packets past an intrusion detection system and firewall. This is due to the way that different systems reassemble packets or handle them when one or more of the same fragments arrive. To better expand on the concept, consider the fact that Windows-based systems give preferential treatment to original fragments, whereas Cisco devices favor the last fragments. Computer-Assisted Attacks and Crimes . Overlapping fragmentation can also be used to facilitate a denial of service. The teardrop attack is an example of this. This fragmentation attack sends packets that are malformed with the fragmentation offset value tweaked so that the receiving packets overlap. The victim does not know how to process these overlapping fragments and so they crash or lock up the receiving system, thereby causing a denial of service. This attack is also quite old and known to affect only Windows 3.Ix, Windows 95, and Windows NT operating systems, as well as the Linux 2.0.32 and 2.1.63 kernels. SYN Flooding SYN Flooding is a DoS attack that exploits a basic weakness found in the Transmission Control Protocol/Internet Protocol (TCP/IP), and its concept is fairly simple. A standard TCP session consists of the two communicating hosts exchanging a SYN I SYN/acknowledgment (ACK) I ACK. The expected behavior is that the initiating host sends a SYN packet, to which the responding host will issue a SYN/ACK and wait for an ACK reply from the initiator.With a SYN attack, or SYN flood, the attacker simply sends only the SYN packet, leaving the victim waiting for a reply. The attack occurs when the attacker sends thousands and thousands of SYN packets to the victim, forcing the victim to wait for replies that never come.While the host is waiting for so many replies, it can't accept any legitimate requests, so it becomes unavailable, thus achieving the purpose of a DoS attack. Some stateful firewalls protect against SYN attacks by resetting pending connections after a specific timeout. Another protection is with the use of SYN cookies, where a computer under attack responds with a special SYN/ACK packet and does not wait for an ACK response. Only when the ACK packet in response to the SYN/ACK packet returns does the entry generate a queue entry from information within the special SYN/ACK packet. Land Attacks The Land attack utilized a weakness in the TCP/IP implementations of a lot of older machines. To execute the attack the attacker sends a TCP SYN packet (a connection initiation), giving the target host's address as both source and destination, and using the same port on the target host as both source and destination. Doing this would create an infinite loop on the vulnerable hosts, causing them to consume all their resources and resulting in a denial of service. Smurf Attacks A Smurf attack is a resource consumption attack using ICMP Echo as the mechanism. ICMP Echo attacks seek to flood the target with ping traffic and use up all available bandwidth. As a result, there is no bandwidth left for available users. Smurf is just one example of an ICMP Echo attack. Smurf exploits ICMP by sending a spoofed ping packet addressed to the network broadcast address and has the source address listed as the victim. On a multi-access network, many systems may possibly reply. The attack results in the victim being flooded with ping responses. Fraggle Attacks Fraggle is the same attack as a Smurf attack, only using User Datagram Protocol (UDP) Echo instead of lCMP Echo. Snork Attacks A Snork attack is another UDP-based DoS attack that's very similar to Smurf and Fraggle, and equally old. In this attack, a specially crafted UDP packet is sent to the Remote Procedure Call (RPC) service (UDP port 135) on a Windows NT server.This can raise the CPU utilization on the server to 100 percent for a short period. Repeated packets sent to the server can keep the utilization at 100 percent. Snork packets could also be bounced between two or more servers to cause high utilization on the network segment, DoS-ing the network as well.
View MoreRecent Posts
Cyberwar and Cyber Terrorism | Part 3
10-10-2020
Cyberwar and Cyber Terrorism | Part 2
10-10-2020