Recent Posts
App Armor walkthrough | The ultimate guardian of Linux machine
AppArmor is a Mandatory Access Control (MAC) system which is a kernel (LSM) enhancement to confine programs to a limited set of resources. AppArmor's security model is to bind access control attributes to programs rather than to users. AppArmor confinement is provided via profiles loaded into the kernel, typically on boot. AppArmor profiles can be in one of two modes: enforcement and complain. Profiles loaded in enforcement mode will result in enforcement of the policy defined in the profile as well as reporting policy violation attempts (either via syslog or auditd). Profiles in complain mode will not enforce policy but instead report policy violation attempts. AppArmor differs from some other MAC systems on Linux: it is path-based, it allows mixing of enforcement and complain mode profiles, it uses include files to ease development, and it has a far lower barrier to entry than other popular MAC systems. AppArmor is an established technology first seen in Immunix and later integrated into Ubuntu, Novell/SUSE, and Mandriva. Core AppArmor functionality is in the mainline Linux kernel from 2.6.36 onwards; work is ongoing by AppArmor, Ubuntu and other developers to merge additional AppArmor functionality into the mainline kernel. In addition to manually creating profiles, AppArmor includes a learning mode, in which profile violations are logged, but not prevented. This log can then be used for generating an AppArmor profile, based on the program's typical behavior. AppArmor is implemented using the Linux Security Modules (LSM) kernel interface. AppArmor is offered in part as an alternative to SELinux, which critics consider difficult for administrators to set up and maintain. Unlike SELinux, which is based on applying labels to files, AppArmor works with file paths. Proponents of AppArmor claim that it is less complex and easier for the average user to learn than SELinux. They also claim that AppArmor requires fewer modifications to work with existing systems.[ For example, SELinux requires a filesystem that supports "security labels", and thus cannot provide access control for files mounted via NFS. AppArmor is filesystem-agnostic. AppArmor represents one of several possible approaches to the problem of restricting the actions that installed software may take. The SELinux system generally takes an approach similar to AppArmor. One important difference, SELinux identifies file system objects by inode number instead of path. Under AppArmor an inaccessible file can become accessible if a hard link to it is created. SELinux's inode-based model would still deny access through newly created hard links because the hard link would be pointing to an inaccessible inode. SELinux and AppArmor also differ significantly in how they are administered and how they integrate into the system. Isolation of processes can also be accomplished by mechanisms like virtualization; the One Laptop per Child (OLPC) project, for example, sandboxes individual applications in lightweight Vserver. In 2007, the Simplified Mandatory Access Control Kernel was introduced. In 2009, a new solution called Tomoyo was included in Linux 2.6.30; like AppArmor, it also uses path-based access control. How AppArmor Works AppArmor works at the kernel level and it loads during the bootup. The way AppArmor handle the permission is via Profiles. Profiles is a set of rules that determines what the program can and cannot do. There are two modes that the Profiles can run: Enforcement and Complain. The Enforcement mode is a strict enforcement of the policy defined in the profile as well as reporting policy violation attempts. Complain mode will only report the policy violation attempts, but does not enforce the policy. Most profiles are loaded in the Enforcement mode, though there can be a good number of third parties profiles that are loaded in the Complain mode as well. Checking out your AppArmor Status If you are using Ubuntu 19.04 or above, AppArmor is installed by default and loads when you boot up your computer. To check the AppArmor status, type the following command in the terminal: sudo apparmor_status AppArmor Profiles In AppArmor, processes are restricted by profiles. The list above shows us the protocols that are installed on the system – these ones come with Ubuntu. You can also install other profiles by installing the apparmor-profiles package. Some packages – server software, for example – may come with their own AppArmor profiles that are installed on the system along with the package. You can also create your own AppArmor profiles to restrict software. Profiles can run in “complain mode” or “enforce mode.” In enforce mode – the default setting for the profiles that come with Ubuntu – AppArmor prevents applications from taking restricted actions. In complain mode, AppArmor allows applications to take restricted actions and creates a log entry complaining about this. Complain mode is ideal for testing an AppArmor profile before enabling it in enforce mode – you’ll see any errors that would occur in enforce mode. Profiles are stored in the /etc/apparmor.d directory. These profiles are plain-text files that can contain comments.
View MoreBackdoor the soul hacker
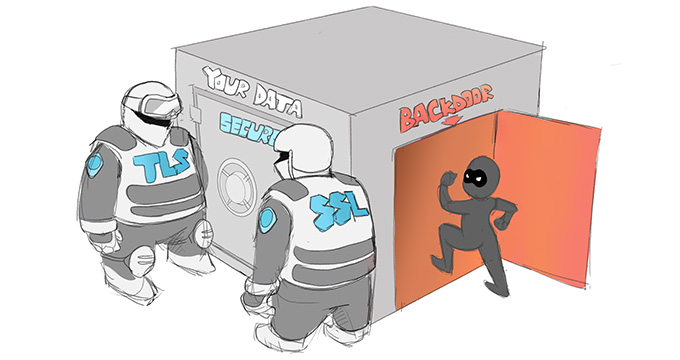
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" tiny computer-within-a-computer such as that found in Intel's AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within auto schediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the firmware of the hardware, or parts of an operating system such as Windows. Trojan horses can be used to create vulnerabilities in a device. A Trojan horse may appear to be an entirely legitimate program, but when executed, it triggers an activity that may install a backdoor. Although some are secretly installed, other backdoors are deliberate and widely known. These kinds of backdoors have "legitimate" uses such as providing the manufacturer with a way to restore user passwords. Many systems that store information within the cloud fail to create accurate security measures. If many systems are connected within the cloud, hackers can gain access to all other platforms through the most vulnerable system. Default passwords (or other default credentials) can function as backdoors if they are not changed by the user. Some debugging features can also act as backdoors if they are not removed in the release version. In 1993, the United States government attempted to deploy an encryption system, the Clipper chip, with an explicit backdoor for law enforcement and national security access. The chip was unsuccessful. Overview The threat of backdoors surfaced when multiuser and networked operating systems became widely adopted. Petersen and Turn discussed computer subversion in a paper published in the proceedings of the 1967 AFIPS Conference.[12] They noted a class of active infiltration attacks that use "trapdoor" entry points into the system to bypass security facilities and permit direct access to data. The use of the word trapdoor here clearly coincides with more recent definitions of a backdoor. However, since the advent of public key cryptography the term trapdoor has acquired a different meaning (see trapdoor function), and thus the term "backdoor" is now preferred, only after the term trapdoor went out of use. More generally, such security breaches were discussed at length in a RAND Corporation task force report published under ARPA sponsorship by J.P. Anderson and D.J. Edwards in 1970.[13] A backdoor in a login system might take the form of a hard coded user and password combination which gives access to the system. An example of this sort of backdoor was used as a plot device in the 1983 film WarGames, in which the architect of the "WOPR" computer system had inserted a hardcoded password which gave the user access to the system, and to undocumented parts of the system (in particular, a video game-like simulation mode and direct interaction with the artificial intelligence). Although the number of backdoors in systems using proprietary software (software whose source code is not publicly available) is not widely credited, they are nevertheless frequently exposed. Programmers have even succeeded in secretly installing large amounts of benign code as Easter eggs in programs, although such cases may involve official forbearance, if not actual permission. A countermeasure against backdoors is open-source software, where the source code can be examined for potential backdoors and it is as such usually harder to ″hide″ a backdoor in there. Combined with reproducible builds one can also be sure that a provided binary corresponds to the publicly available source code Countermeasures Once a system has been compromised with a backdoor or Trojan horse, such as the Trusting Trust compiler, it is very hard for the "rightful" user to regain control of the system – typically one should rebuild a clean system and transfer data (but not executables) over. However, several practical weaknesses in the Trusting Trust scheme have been suggested. For example, a sufficiently motivated user could painstakingly review the machine code of the untrusted compiler before using it. As mentioned above, there are ways to hide the Trojan horse, such as subverting the disassembler; but there are ways to counter that defense, too, such as writing your own disassembler from scratch. A generic method to counter trusting trust attacks is called Diverse Double-Compiling (DDC). The method requires a different compiler and the source code of the compiler-under-test. That source, compiled with both compilers, results in two different stage-1 compilers, which however should have the same behaviour. Thus the same source compiled with both stage-1 compilers must then result in two identical stage-2 compilers. A formal proof is given that the latter comparison guarantees that the purported source code and executable of the compiler-under-test correspond, under some assumptions. This method was applied by its author to verify that the C compiler of the GCC suite (v. 3.0.4) contained no trojan, using icc (v. 11.0) as the different compiler.[24] In practice such verifications are not done by end users, except in extreme circumstances of intrusion detection and analysis, due to the rarity of such sophisticated attacks, and because programs are typically distributed in binary form. Removing backdoors (including compiler backdoors) is typically done by simply rebuilding a clean system. However, the sophisticated verifications are of interest to operating system vendors, to ensure that they are not distributing a compromised system, and in high-security settings, where such attacks are a realistic concern.
View MoreLet's Understand the Firewall
In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted internal network and an untrusted external network, such as the Internet. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls filter traffic between two or more networks and run on network hardware. Host-based firewalls run on host computers and control network traffic in and out of those machines. History The term firewall originally referred to a wall intended to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to a network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were the routers used in the late 1980s, because they separated networks from one another, thus halting the spread of problems from one network to another. Before it was used in real-life computing, the term appeared in the 1983 computer-hacking movie WarGames, and possibly inspired its later use Screenshot of Gufw: The firewall shows its settings for incoming and outgoing traffic. The first reported type of network firewall is called a packet filter. Packet filters act by inspecting packets transferred between computers. When a packet does not match the packet filter's set of filtering rules, the packet filter either drops (silently discards) the packet, or rejects the packet (discards it and generates an Internet Control Message Protocol notification for the sender) else it is allowed to pass.[6] Packets may be filtered by source and destination network addresses, protocol, source, and destination port numbers. The bulk of Internet communication in the 20th and early 21st century used either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) in conjunction with well-known ports, enabling firewalls of that era to distinguish between, and thus control, specific types of traffic (such as web browsing, remote printing, email transmission, file transfer), unless the machines on each side of the packet filter used the same non-standard ports. The first paper published on firewall technology was in 1987 when engineers from Digital Equipment Corporation (DEC) developed filter systems known as packet filter firewalls. At AT&T Bell Labs, Bill Cheswick and Steve Bellovin continued their research in packet filtering and developed a working model for their own company based on their original first generation architecture Hardware and Software Firewalls Firewalls can be either hardware or software but the ideal configuration will consist of both. In addition to limiting access to your computer and network, a firewall is also useful for allowing remote access to a private network through secure authentication certificates and logins. Hardware firewalls can be purchased as a stand-alone product but are typically found in broadband routers, and should be considered an important part of your system security and network set-up. Most hardware firewalls will have a minimum of four network ports to connect other computers, but for larger networks, a business networking firewall solution is available. Software firewalls are installed on your computer, like any software program, and you can customize it; allowing you some control over its function and protection features. A software firewall will protect your computer from outside attempts to control or gain access to your computer. Firewalls may also be a component of your computer's operating system. For example, Windows Firewall is a Microsoft Windows application that notifies users of any suspicious activity. The app can detect and block viruses, worms, and hackers from harmful activity Firewall Filtering Techniques Firewalls are used to protect both home and corporate networks. A typical firewall program or hardware device filters all information coming through the Internet to your network or computer system.
View MoreRecent Posts
Cyberwar and Cyber Terrorism | Part 3
10-10-2020
Cyberwar and Cyber Terrorism | Part 2
10-10-2020