Way to Darker side of internet | Best way to access darknet
What is a Virtual Private Network?
Before we explore what VPNs are, let’s establish the link between the internet and security. Most public networks such as the Wi-Fi that you’re using in your office are susceptible to traffic analysis. There are always unseen “online” eyes everywhere if you are using these networks.
Traffic analysis may emanate from government agencies such as FBI or CIA—that may interested in monitoring your online movements—or private corporations that want to target you with their “boring” products or services. But that’s not all. The majority of Internet Service Providers (ISPs) may also be monitoring your internet activities to promote their services.
This means that at the very least, you should protect your data such as credit card details, usernames, and passwords particularly if you’re using a public network.
The Tor and VPN can help you protect your private data as you remain anonymous while accessing the internet. So, what is a VPN? A VPN is a network connection that is established to provide a secure link to another location (usually a remote location).
A VPN creates the illusion that you are connecting from a different place, therefore, malicious internet users may not know what’s being transmitted across the internet. Ideally, your computer will create an encrypted virtual tunnel that connects to the VPN server from where the entire internet traffic is channelled.
Once the private connection has been linked to the VPN server, all the communication that takes place on the network will appear as though coming from the VPN server, but in the real sense, it’s coming from your computer.
This keeps your data from being exposed to eavesdroppers that may be interested in tapping the data in transit. Why may you want to use a VPN instead of the public networks?
First, you can use a VPN to connect securely to any remote network through the web. If you have employees who want to access some files, applications and other resources such as printers, then installing a VPN will be helpful if you don’t want to compromise on security.in fact, you can set up a VPN to access your home network if you’re ever traveling. Second, VPNs can help to connect several networks together in a secure manner.
In fact, you can use a VPN to share servers and other networked resources such as printers that may be located in different places. If you’re an organization, then VPN’s can help you connect multiple intranets for the promotion of your bottom line.
Third, VPNs can help you improve your online privacy and anonymity. If you’re connected to a public network such as Wi-Fi, then the communication may be untrusted.
A VPN can help you secure such communication because it encrypts the internet traffic, therefore, helping you to maintain your privacy while you remain anonymous while online.
Lastly, a VPN can help to circumvent regional internet restrictions—what’s commonly known as geo blocking—on some sites. Some authoritarian governments or even private corporations may place restrictions on some sites.
VPN’s can help you to bypass such restrictions. In fact, several journalists have used VPNs to sidestep state sponsored website censorship in the majority of authoritarian states.
What is the difference between TOR and VPNs?
The differences between Tor and VPNs are multi fold. First, Tor networks contain several volunteer nodes that transmit data from the entry computer (source) to the exit node which is the destination computer. It allows the client computers to conceal their status through configurations of the volunteer nodes (Tor servers) which links up with the Tor workstations.
The Tor Server doesn’t need to provide its IP address and so does the client. Instead, the network uses the onion address—a 16 character code that a client has to enter instead of the conventional URL. On the other hand, VPN networks don’t use volunteer nodes to relay data between the client and the server. It’s basically an into-the-tunnel and out-of-the-tunnel network that encrypts whatever communication is taking place.
In other words, if you trust the VPN provider for data privacy and anonymity, then it is. Second, Tor networks tend to be slow compared to VPNs.
This is because the information that is sent from one computer to another must be encrypted every time it passes a volunteer Tor node. This slows down the communication process. Although encryption is also handled in VPNs, the encryption process doesn’t occur at every node. Third, Tor networks will always guarantee privacy and anonymity.
This is because of the manner they operate. For instance, the Tor server doesn’t need to provide its IP address and so does the client. Instead, the network uses the onion address—a 16 character code that a client has to enter instead of the conventional URL.
This will guarantee your privacy and anonymity. On the other hand, the type of VPN provider you choose for your services dictates the quality of the services. Therefore, it’s vital that you select a quality VPN provider that doesn’t store communication logs.
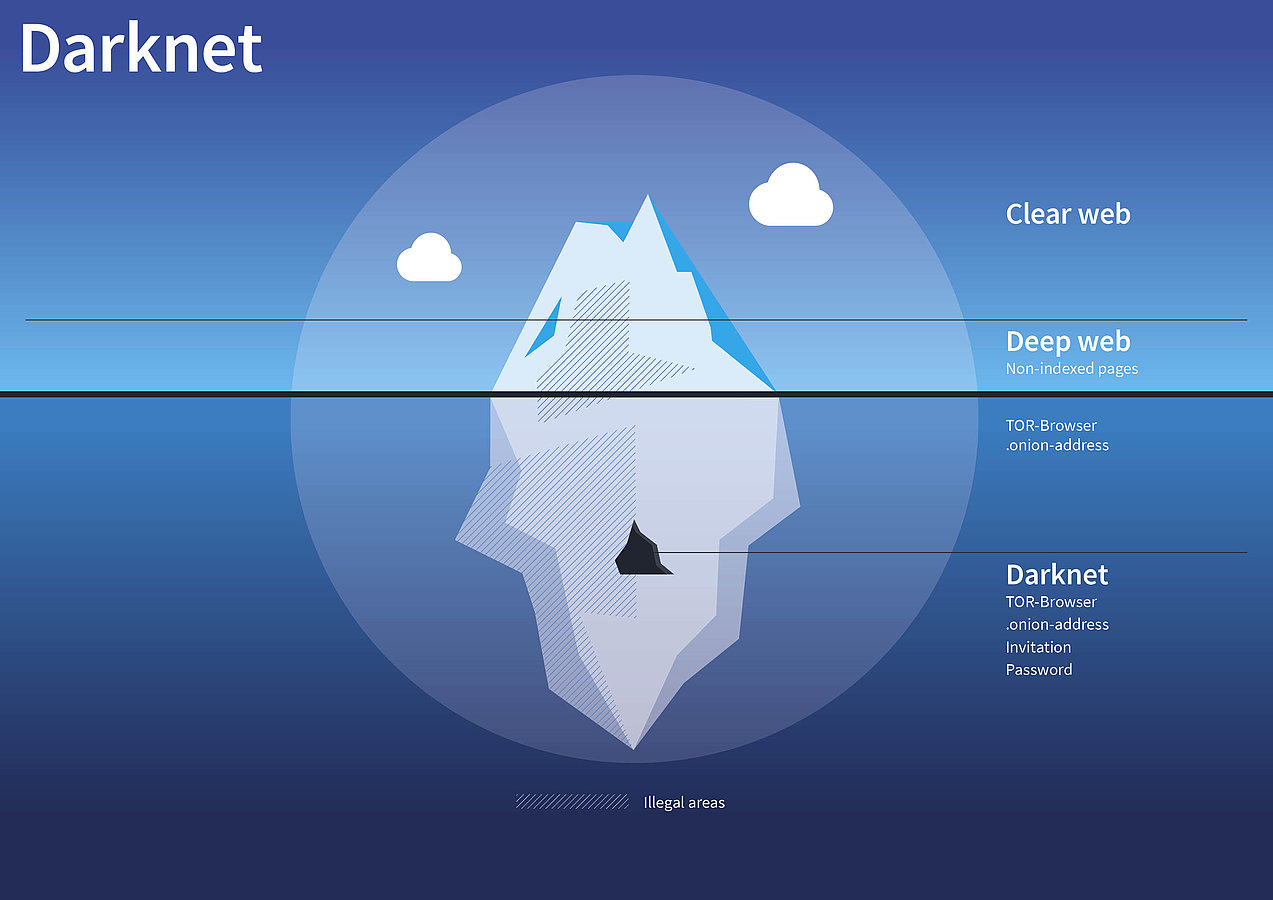
This is because the communication logs can still be accessed therefore exposing the communication between the client and the server. Finally, Tor networks can help you to access the Deep Web. The Tor protocol enables the clients to hide their status (IP addresses) by configuring the server to link up with the Tor workstations using the Tor relay. The server doesn’t need to provide its IP address and so does the client. Instead, the Tor network uses the onion address that a client has to enter instead of the conventional URL.
Since these networks have several famous Deep Web data, clients can access them through the Tor relay. Conversely, VPNs can’t access any Deep Web or Darknet. Other protocols that can access the Deep Web Now that you’ve learned how Tor works and the differences between Tor and VPNs, let’s dig deeper to find out which other protocols can be used to access Deep Web.
Below are other protocols that can enhance privacy and anonymity while online while also allowing users to access Deep Web:
#1: I2P
I2P, which is an acronym for Invisible Internet Project, is a protocol that was started way back in in 2003, to promote anonymity of internet users. All I2P networks aren’t accessible from any regular computer unless special software is installed on such computers. When you install I2P software on your computer, you’ll begin to route internet traffic through the I2P system just like a Tor relay.
The I2P system encrypts the communication by creating a distributed, decentralized and dynamic network that enables secure communication between the client and server. You can also use the I2P network to circumvent state sponsored website censorship in the majority of authoritarian states. Is I2P network different from Tor? Yes.
I2P networks route web traffic differently compared to Tor. At the heart of I2P is packet-based routing system as opposed to the Tor’s circuit-based routing. This means that there’s no dedicated route between the client and the server as we saw in Tor relays where the Tor servers establish a dedicated path through which the traffic is routed.
Because of packet-based routing, the traffic can be routed dynamically in a distributive manner as opposed to the Tor relay. This offers a higher level of reliability to the network. In addition, the I2P network doesn’t rely on the trusted directory service to obtain its route information. Instead, the network routes are created dynamically and updated regularly.
#2: Freenet
Freenet is a fully peer-to-peer, distributed, anonymity publishing network that offers secure means to store data. Besides providing anonymity, Freenet allows internet users to create applications that ride on its platform to develop more generic and anonymous communications. Such applications include static websites and online message boards.
Contrasted with to I2P, Freenet provides some substantial benefits. Besides, its distributed data store, it allows users to get the content that’s published by others even if the publisher isn’t connected to the internet.
While there’s an overlap of users who simply want to share data with each other anonymously in Freenet, I2P systems don’t offer such services to their users.